The week of Monday 7 to Sunday 13 October was spent in Melbourne, primarily covering the Australian Cyber Conference. Despite a lingering sore throat, I managed to squeeze out four stories for ZDNet and have a pleasant weekend. Excellent!
Continue reading “Weekly Wrap 489: A week in Melbourne with cybers”The 9pm Get Some Goddam Perspective

For nearly two weeks now, Australians have been more afraid of the fear of the risk of terror that ever before. We’re going to war, and the defence minister is an idiot. But don’t worry about why an event on the other side of the world is suddenly a threat here. We’re going to go butt chugging.
What does any of this mean? Who knows.
But we do hear how terrorism alert rankings serve no purpose beyond encouraging a burst of panic and how we won the war on Thai chilli sauce, as well as the evacuation of the Westfield Burwood shopping centre and how that did not relate to any contemporary issue.
Continue reading “The 9pm Get Some Goddam Perspective”Weekly Wrap 160: Black dog, black sky and more NSA
 My week Monday 24 to Sunday 30 June 2013 was rather complicated, at least emotionally.
My week Monday 24 to Sunday 30 June 2013 was rather complicated, at least emotionally.
As will be explained tomorrow on Tuesday Thursday.
Nevertheless, I managed to create some media objects along the way. And here they are.
Podcasts
I’m very pleased to have launched my new podcast and website, Corrupted Nerds.
- Corrupted Nerds: Conversations 1, a conversation with Eugene Kaspersky, founder and CEO of Kaspersky Lab. If we’re going to be accurate, then this was really published in the previous week. But I forgot. So sue me.
- Corrupted Nerds: Extra 1, being Senator Brett Mason’s “corrupted nerds” speech in the Australian Senate from 21 August 2012, which inspired the title. This was published last week too.
- Corrupted Nerds: Conversations 2, a chat with Sean Richmond, senior technology consultant from Sophos Australia and New Zealand, about personalised malware, defense in depth, and why advanced persistent threats (APTs) and cyberwar are over-hyped.
I have yet to arrange any funding for this podcast, so I’ll be seeking that soon — and I’d be more than happy to hear your suggestions.
Articles
- Remember the NSA? Snooping is the real story, Crikey, 25 June 2013, in which I point out that the global hunt for Edward Snowden is in fact a distracting narrative.
- Beyond Conroy: Australia’s future internet politics, ZDNet Australia, 28 June 2013, in which I look at the issues that will need to be tackled by any future Australian communications minister.
- Schneier joins EFF board in wake of NSA scandal, CSO Online, 28 June 2013. Bruce Schneier’s EFF move sends a powerful message.
Media Appearances
None.
Corporate Largesse
- Since Saturday 8 June I’ve been using Vodafone’s new 4G network while in Sydney, and their existing 3G network while in the Blue Mountains, with a Samsung Galaxy S4 handset that they’ve loaned me.
I’ll be writing about my experiences on Monday.[Update 2 July 2013: I’ve just posted my write-up of my experiences. Yeah, it’s Tuesday.
The Week Ahead
The new financial year starts on Monday, so I daresay the morning will be full of administrivia. I’ll then be heading down to Sydney, because…
On Tuesday morning I’m attending a discussion on data sovereignty and the cloud, hosted by data centre firm NEXTDC, along with financial services company Aon and law firm Baker & McKenzie. That will be followed at the same event by the launch of the University of New South Wales’ report Data Sovereignty and the Cloud — A Board and Executive Officers’ Guide. I’ll be reporting this for someone, but as yet I don’t know who that will be.
I’ll be in Sydney again later in the week, probably Thursday, for a medical appointment, but that’s not confirmed yet. When it is, I’ll arrange my writing and media production schedule around that. There’s definitely stories to write for ZDNet Australia and CSO Online, plus an episode of Corrupted Nerds, and there’ll certainly be things that pop up along the way.
And then the weekend is unplanned.
[Photo: Sydney under the clouds, photographed from the Rydges Camperdown hotel in Sydney on 25 June 2013.]
So China hacked some US newspapers…
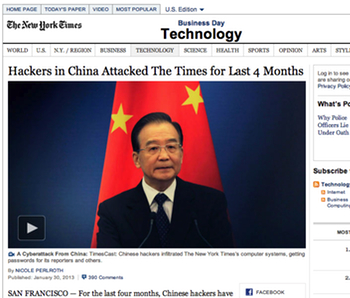 On 31 January The New York Times reported that it had been hacked by China, their networks penetrated for some four months. The Wall Street Journal and Washington Post too. So naturally I ended up writing about it.
On 31 January The New York Times reported that it had been hacked by China, their networks penetrated for some four months. The Wall Street Journal and Washington Post too. So naturally I ended up writing about it.
For Crikey I wrote China not the only ones taking part in cyber spookery, which puts these attacks in the context of the online espionage and sabotage operations of recent years.
“Countless organisations have experienced the same scenario in recent years,” I wrote. “But it’s big news this time because journalists were the targets.” Cynical, perhaps, but I gather security über-expert Bruce Schneier said much the same thing, so I’m kinda chuffed.
And for CSO Online I wrote Chinese attacks show up useless infosec, again.
“Recent attacks on US newspapers are further proof that, despite making billions, the information security industry is pretty much screwed,” it begins. That one won’t make me any friends. So nothing new there.
I must admit, I found both stories fairly straightforward to write. I guess I’ve been writing about this stuff long enough to feel confident about it.
China has denied the accusations, of course.
As it happens, this week’s On the Media podcast from WNYC begins with a six-minute backgrounder on the hacks which is well worth the listen.
Why tweeting my movements isn’t a safety risk
[Update 2.25pm: Comments on Twitter have persuaded me to emphasise that the question here is specifically about “personal safety” only, not lame and replaceable possessions, and my personal safety at that. As the second-last paragraph says, the risk profile might not be the same for everyone. These are the choices I’ve made with open eyes.]
 “How do you think that tweeting your day plans affects your personal safety?” asked Ravneel Chand a short time ago. Overall, I reckon it actually increases my safety. Here’s why.
“How do you think that tweeting your day plans affects your personal safety?” asked Ravneel Chand a short time ago. Overall, I reckon it actually increases my safety. Here’s why.
Background first. Here’s today’s “daily plan” tweet which, like those on pretty much every other day, is tweeted shortly before I settle down to work.
Thu plan: Bump out Waratah Cottage; 1032 train to Sydney; lunch (where?); errand Newtown/Enmore; write something; evening TBA.
Later in the morning I mentioned that I’d be catching a later train. And then, just as I left the house:
Mobile: Cab, shortly, to Wentworth Falls; 1132 train to Sydney Central; train to Town Hall station; 1335 walk to SEKRIT hotel and check in.
Clearly the fear being expressed is that by knowing my movements some bad person could more easily do me harm. But let’s do a proper risk assessment. You start one of those by enumerating the risks, and then you look at how this additional information might change those risks.
Continue reading “Why tweeting my movements isn’t a safety risk”
RSA Conference keynotes: a personal viewing guide
All of the keynote sessions from the RSA Conference on information security are now online as video and audio. Here’s my personal suggestions for the ones to watch.
I didn’t see all of these keynotes. Sometimes there were 17 or 18 sessions running in parallel. I also skipped most of those that were obviously a vendor telling their story. Once I saw a couple of them, I was reminded that for so many IT folks the word “keynote” doesn’t mean something that provides insight any more, but is merely a synonym for “infomercial”.
It’s a shame that RSA hasn’t provided the media in an embeddable form. Or provided an obvious way to link to each keynote directly. Or given the keynote titles. Or told you which ones are panel discussions rather than single-person presentations.
But here’s what I reckon you should watch.
- Wednesday’s panel led by James Lewis, “Cyberwar, Cybersecurity, and the Challenges Ahead”, with former NSA head Mike McConnell, former US Secretary of Homeland Secretary Michael Chertoff and security guru Bruce Schneier.
- The Cryptographers Panel with Dickie George, Whitfield Diffie, Adi Shamir, Martin Hellman and Ronald Rivest. I didn’t see this one myself, but from the comments on Twitter it was a must-see tour through the history of cryptography and an informed look into the future.
- The presentations by US Deputy Secretary of Defence William Lynn and the head of US Cyber Command General Keith Alexander. Lynn’s presentation was a little dry but set out US political views. Alexander was witty and expanded on Lynn’s comments into the practical realm.
- Microsoft’s Scott Charney’s presentation of their “Collaborative Defence” strategy, important because this is the worldview that Microsoft is encouraging us to adopt.
- Michio Kaku, physicist and best-selling author, on “The Next 20 Years: Interacting with Computers, Telecommunication and AI in the Future”. I didn’t see this one, but I’ve seen Kaku on The Colbert Report and he’s a damn good presenter.
- Michael Capuzzo, author of The Murder Room, on forensic pathology. Again, I didn’t catch this one, but was told it was fascinating.
- Bill Clinton’s “Embracing our Common Humanity”. My understanding — although I haven’t checked yet — is that this is essentially the same speech that he gave at Dreamforce in December. That said, he’s a persuasive speaker and it’s worth a listen.
That’s my personal selection, based on what I saw or what I heard about? What are your selections?
[Photo: James Lewis’ keynote panel, “Cyberwar, Cybersecurity, and the Challenges Ahead”. From left to right: former NSA head Mike McConnell; former US Secretary of Homeland Secretary Michael Chertoff; and security guru Bruce Schneier. Disclosure: I travelled to San Francisco to attend the RSA Conference as a guest of Microsoft.]


