“A creator, such as an artist, musician, photographer, craftsperson, performer, animator, designer, videomaker, or author — in other words, anyone producing works of art — needs to acquire only 1,000 True Fans to make a living.”
So says Kevin Kelly, founder of Wired magazine, in his latest essay 1000 True Fans.
It’s worth reading the full essay to completely grok what he’s on about. But in brief, a “true fan” is someone who’ll purchase anything and everything you produce.
They will drive 200 miles to see you sing. They will buy the super deluxe re-issued hi-res box set of your stuff even though they have the low-res version. They have a Google Alert set for your name. They bookmark the eBay page where your out-of-print editions show up. They come to your openings. They have you sign their copies. They buy the t-shirt, and the mug, and the hat. They can’t wait till you issue your next work. They are true fans…
Kelly’s point is that the Internet allows you to find and stay in touch with True Fans cheaply and easily — globally. He gives some useful numbers to help think it through, and points to some examples which are already working.
The trick is making direct contact with the fans out there in the long tail, converting a thousand Lesser Fans into a thousand True Fans.
Assume conservatively that your True Fans will each spend one day’s wages per year in support of what you do. That “one-day-wage” is an average, because of course your truest fans will spend a lot more than that. Let’s peg that per diem each True Fan spends at $100 per year. If you have 1,000 fans that sums up to $100,000 per year, which minus some modest expenses, is a living for most folks.
One thousand is a feasible number. You could count to 1,000. If you added one fan a day, it would take only three years. True Fanship is doable. Pleasing a True Fan is pleasurable, and invigorating…
Of course that magic number might not be 1000 for you. It might be 500 or 5000. But the principle is the same.
Kelly has researched the history of this, too. He’s discovered a First Monday essay from 1999 where John Kelsey and Bruce Schneier call it the Street Performer Protocol. And in 2004 author Lawrence Watt-Evans used this model to publish a novel — adding a chapter a month through fan subscriptions. There’s plenty more examples.
He also points to Fundable, a web-based organisation which…
…allows anyone to raise a fixed amount of money for a project, while reassuring the backers the project will happen. Fundable withholds the money until the full amount is collected. They return the money if the minimum is not reached.
Kelly reckons that an artist shouldn’t find it too hard to nurture 1000 True Fans globally. It certainly beats poverty. And it’s certainly made an impact upon my thinking! [full essay]
[Update: By an odd coincidence, this is my 1000th blog post — and it has “1000” in the title. Is that significant, do ya think?]

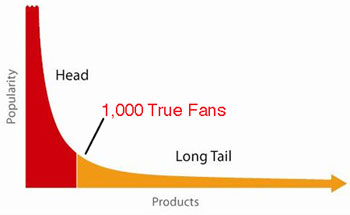
What does that popularity versus products graph mean?
The red colouring and the red label suggest that the 1000 fans can be found in the red area, implying that “popularity” is rather some measure of loyalty.
The axes suggest otherwise.
The original article doesn’t help.
Care to describe that graph in words?
The original article doesn’t help. But the original original does. 🙂
Purchase rate for the vertical axis — a type of popularity.
Product ordered by popularity rank for the horizontal.
So the red area represents sales of popular stuff. The yellow area less popular stuff. And the long tail means the unpopular stuff outsells the popular — a greater total, but far less per product. The new model.
Fair enough.
And the “1000 True Fans” label written in red? Well, being an engineer I actually believed some thought had gone into it! My mistake. Better to re-read it as “hiding in this vast yellow area are your 1000 true fans”.
FYI:
http://www.wired.com/wired/archive/12.10/images/FF_170_tail2_f.gif
@Mat F: Ah, you’ve answered your own question! 😉 I was going to say that the graph is a religious symbol, brandished by people showing that they follow the neo-economic belief systems of The Long Tail. It’s like having a fish sticker on your car if you’re a certain kind of Christian.
Less seriously…
Your description is correct. The idea is that with global ordering and digital delivery, with many products and services it’s now cheaper to service that long tail of minority interests. The market isn’t only about “a few big blockbusters”: you can also service a huge number of low-ranking interests.
Kevin Kelly distorts it in his presentation, where the horizontal axis is probably something like “people who buy stuff from you, ranked by the amount they buy”, and the vertical axis is “how much that person spends”. His thesis is that an artist can, though nurturing the fans, turn some of that long tail of low-spending folks into one of the few big-spenders you need to survive.
Hi Stilgherrian, I’ll be your fan!