 My legal name, a single word or “mononym” that’s a given name, with no surname, isn’t handled well by poorly-designed bureaucratic information systems — that is, the usual kind. Today I launch Adventures in Identity, a blog series where I politely request every guilty organisation to fix the problem — and post their responses.
My legal name, a single word or “mononym” that’s a given name, with no surname, isn’t handled well by poorly-designed bureaucratic information systems — that is, the usual kind. Today I launch Adventures in Identity, a blog series where I politely request every guilty organisation to fix the problem — and post their responses.
First up, our corporate regulator, the Australian Securities and Investment Commission (ASIC), and in particular their ASIC Connect online service.
This was drawn to my attention because the registration for one of my business names, Skank Media, is due for renewal — and ASIC Connect is the easiest way to do it.
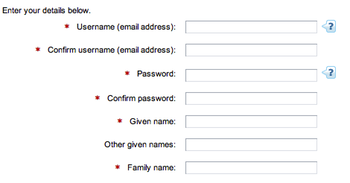 The first problem I encountered is that ASIC Connect’s account creation form has both “Given name” and “Family name” as required fields, so immediately I must enter something other than my legal name to create an account — although to ASIC’s credit, the rest of the process was painless.
The first problem I encountered is that ASIC Connect’s account creation form has both “Given name” and “Family name” as required fields, so immediately I must enter something other than my legal name to create an account — although to ASIC’s credit, the rest of the process was painless.
ASIC had previously sent me a letter with an “ASIC key” that linked this new account to my existing ASIC business name record.
I have another business name, Prussia.Net, so I decided to link that in too. But ASIC Connect wouldn’t let me. My name didn’t match the name of the registrant of Prussia.Net. Really?
Sure enough, while Skank Media is now registered to “Stilgherrian Stilgherrian”, and it was previously registered to “Mr Stilgherrian”, Prussia.Net is registered to “_____ Stilgherrian”. Five underscores! What an excellent work-around.
Then when I tried to link both business names to my Australian Business Number (ABN), the basic business identifier for entities other than registered companies — I’m a sole trader — that’s now listed as “Stilgherrian Stilgherrian”. It was once correct, though, as an historical ABN search shows a single-name version from 4 October 2000 to 27 February 2010. See the attached PDF.
One of key problems with this mess — apart from the untidy data that makes it look like something shonky is going on — is that these are all legal records. “To the best of my knowledge, the information supplied in this transaction is complete and accurate (it is an offence to provide false or misleading information to ASIC),” we are warned. But I can’t do that.
As I write this, it’s still before 0900 AEST, so my tweets directed to @ASIC_Connect have yet to receive a reply. They may well have a straightforward way to sort this out. Stay tuned.
I should also point out that in ASIC’s defence, they’ve recently merged data from state-based business name registries, cross-matching it with the Australian Business Register — and the latter was notoriously inaccurate.
[Update 1415 AEST: I just got a call from the ASIC staffer who was monitoring their Twitter account earlier today. This isn’t the first time they’ve encountered a mononym, but so far they’ve just carried across records from the state databases so left the work-arounds in place. In my case, they have to cleanse the data so all my records match — and they’ll need to decide on a policy so that similar cases are handled uniformly in the future. So I sent them some photo ID, and they’ll take it from here, and let me know what they decide. Pleased.]
[Update 1620 AEST: The ASIC staffer just called again. They have a system. The back-end database can handle mononyms, it’s just that the web front end has the more stringent input validation. So they’ve settled on putting “Stilgherrian” in the given name field, and a single underscore “_” in the family name field, so I can still enter something and get a match. They’ve manually updated all my records, and now I should be able to merge them. Now that’s service.]
Note: I’ve previously called ASIC incompetent and reckless, calling for a head on a spike, but that was a completely unrelated matter. Obviously.
 I’d scheduled time tonight to write about my crowdfunded journalism project — the initial target was achieved in under 17 hours! — but after a complex day I’m mentally exhausted.
I’d scheduled time tonight to write about my crowdfunded journalism project — the initial target was achieved in under 17 hours! — but after a complex day I’m mentally exhausted.



