My week of Monday 10 to Sunday 16 June 2019 included another lovely trip to Canberra, but also an annoying viral bug that wiped me out for a whole day on Friday, and then work days on Saturday and Sunday. Balance?
Continue reading “Weekly Wrap 472: Canberra, with cybers and a virus”Not hacked, bugs
It turns out that my technical difficulties the other day were in all likelihood not the result of being hacked but an arsehat software incompatibility.
The short version is that the weirdnesses I experienced were caused by:
- OS X Lion has known problems dealing with certain PDF files. It appears that the problematic PDF, produced by OpenOffice.org and then emailed via a Mailman mailing list, was one of them. Hence Apple Mail and sometimes Preview would crash when dealing with this PDF.
- Norton Internet Security for Mac version 4 is only for OS X up to Snow Leopard. OS X Lion requires Norton Internet Security for Mac version 5. It’s a shame neither NIS nor Lion knew this.
- Norton Internet Security probably hadn’t updated its virus definitions in the previous week because I was travelling a fair bit and was probably offline at the scheduled time.
I determined all this while I was running backups. It’s always sensible to make sure your backups are in order before doing any significant technical work.
I discovered that:
- Copying the 400GB of Time Machine backups of my old MacBook Pro from one external USB drive (pocket sized) to another (bulkier, for archiving) using the Finder took more than 7 hours.
- Creating the initial Time Machine backup of my new MacBook Pro on the pocket USB drive, some 220GB of data, took a little over three hours.
- Encrypting that 640GB USB drive took 14.5 hours.
In hindsight, I suppose I should have checked software compatibility when transferring everything from the dead Snow Leopard machine to Lion, but then it did flag other stuff as incompatible so I assumed… yeah, I know.
Live Blog: How pwned am I?
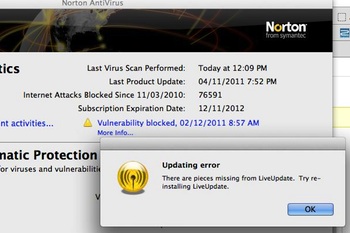 Uhoh. My MacBook Pro may have been hacked. I’ve already done a bit of troubleshooting, but this looks like it’s going to be A Thing, so I’ve decided to liveblog it. And here’s the liveblog.
Uhoh. My MacBook Pro may have been hacked. I’ve already done a bit of troubleshooting, but this looks like it’s going to be A Thing, so I’ve decided to liveblog it. And here’s the liveblog.
The brief version is that Apple Mail crashed when it tried to open a particular email message dated 4 November, one containing a PDF file. Consistently. So I thought I’d do a virus scan on it.
That’s when Norton Internet Security reported that LiveUpdate was missing pieces, and I saw that it hadn’t checked for updates since… 4 November. Eek.
Now all the action would have happened on my battered old MacBook Pro running OS X 10.6 Snow Leopard. That computer finally died of motherboard failure on 11 November and I replaced it with a fresh OS X 10.7 Lion machine on 12 November.
However I did just transfer everything across using Apple’s migration tool, rather than freshly installing all the software and just copying the data, so… well… who knows what the hell is going on?
Deep in my heart I suspect that it was just bugginess and a dying computer, copied badly to a new computer. I hope.
If you want to follow or even help, the liveblog is over the jump.
[Update 11.20pm: Things may not be as bad as I thought. It turns out that Norton Internet Security for Mac version 4.x is only compatible for OS X up to version 10.6 Snow Leopard. There’s NIS version 5.x for OS X 10.7 Lion. It looks like it’s a straightforward software compatibility problem, and the lack of updates could be because I was travelling that week and the computer was offline when updates were scheduled. If this is all the case, I’m a bit disappointed that the software itself couldn’t figure this out.]
Visiting Microsoft HQ to talk security: what should I ask?
I’m off to America! Some tin-pot little IT start-up called Microsoft has invited me to visit their headquarters in Redmond, Washington (pictured) to find out what they’re doing about security, and in particular their Trustworthy Computing initiatives.
Now if you’re a crusty old network administrator like me, you may think that “Microsoft” and “security” in the same sentence is an oxymoron. A decade ago I was building Linux-based firewalls and, like so many people doing the same, I referred to Windows-based computers as “the targets”. And certainly the vast majority of the world’s malware is targeted at Windows.
But I’ve always though that the simplistic “Windows is bad, m’kay” was a bit, well, simplistic. Information security isn’t just about the technology, it’s also about people. Human factors are also the weakest link. And over the years I’ve found that people who throw around those tired platform-wars slogans usually aren’t up to date when it comes to the things they love to hate.
So, I’m off to Redmond later this month to spend three days with some of Microsoft’s engineers and developers, including briefing sessions with senior executives from Microsoft’s Trustworthy Computing Group.
Continue reading “Visiting Microsoft HQ to talk security: what should I ask?”
Crikey Clarifier: Spam

If you think spam is about selling the products being advertised, in most cases you’d be wrong. The real spam business is very different.
I’m in Crikey today with a Crikey Clarifier: What is spam and where does it come from? Amongst other things, I point out:
An estimated 94% of all email is spam: over 100 billion messages every day. Some of that is advertising by businesses who don’t realise it’s wrong or, imagining a sudden surge of business, don’t care.
But over 80% of spam is sent by fewer than 200 people using networks of “borrowed” computers called botnets. These zombie computers have been infected with a virus or Trojan horse that hands control of the computer to the bad guys.
It’s free for all to read.
Big Scary, Little Scary
Which of these images do you find the most frightening? Which the most beautiful? Which the most relevant to human existence?
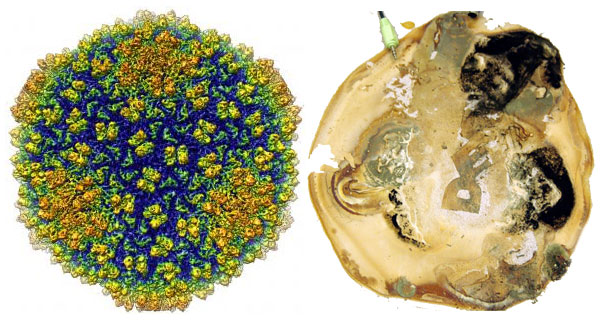
On the left, the highest-resolution image of a virus ever taken. It’s the Epsilon 15 Bacteriophage (i.e. a virus which infects bacteria), and if you count viruses as being alive then it’s one of the most abundant forms of life on Earth.
On the right, a photo of what one guy found growing under his co-worker’s computer monitor. There’s a full image gallery. Hat-tip to Boing Boing.


